Navigating a software bill of materials (SBOM) was like opening a map to every hidden corner of my project’s code. It felt empowering to see each dependency clearly, giving me confidence to tackle vulnerabilities head-on, like spotting weak links in a chain before they could snap.
A software bill of materials is like a recipe card for your code, listing every ingredient or dependency in your project. It helps you track and manage what’s inside, making it easier to catch issues before they boil over.
In this article, we discussed the importance of a Software Bill of Materials (SBOM) for security, compliance, and transparency in software development. We also explored best practices and how SBOMs help manage risks and dependencies effectively.
Introduction To Software Bill Of Materials
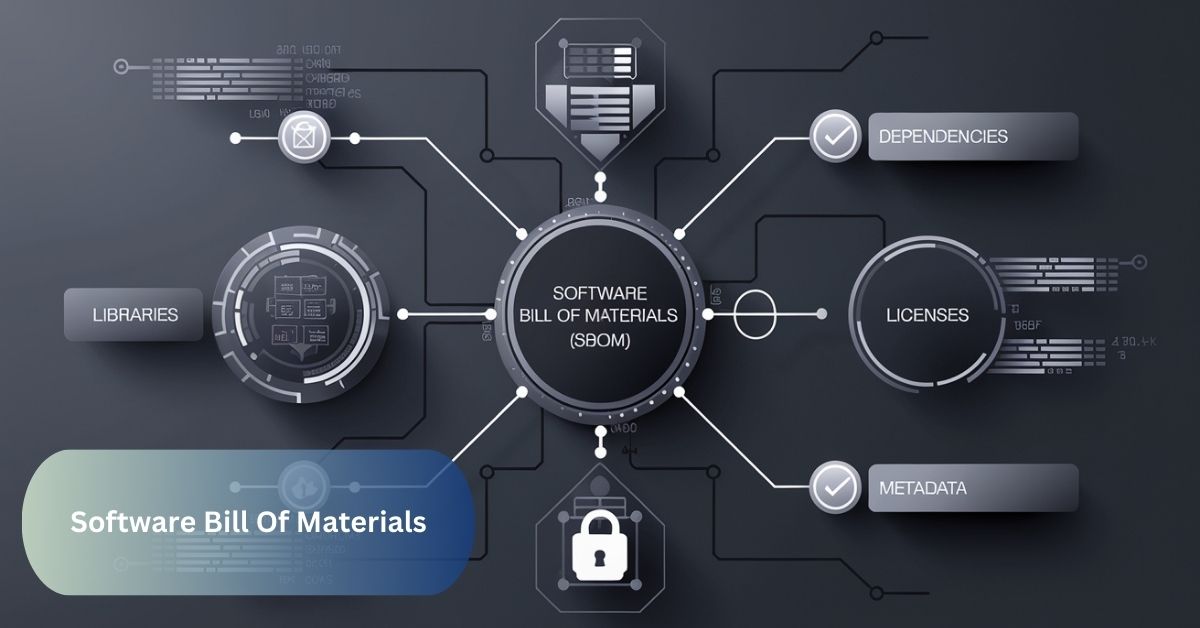
A Software Bill of Materials (SBOM) is a detailed list that lays out every component and dependency within a software project, much like a product’s ingredient label. It provides a clear snapshot of what’s inside, making it easier to track updates, identify vulnerabilities, and ensure compliance. With an SBOM, teams can manage software health proactively, spotting risks early. It’s an essential tool for building transparency and trust in modern software development.
What Is A Software Bill Of Materials?

A Software Bill of Materials (SBOM) is a complete inventory of all components used in a software project, listing each part and its source. It helps developers and security teams see exactly what’s inside, making it easier to manage updates and address security risks. Essentially, an SBOM brings clarity and control to the software’s inner workings.
Software Bill Of Materials Explained
- A Software Bill of Materials (SBOM) is essentially a detailed inventory of every component that makes up a software application. It includes all the libraries, dependencies, and parts, giving a clear view of what’s inside the software.
- Purpose: It helps developers track and manage the ingredients of a software project, ensuring transparency and easier maintenance.
- Security: By identifying all parts, it allows teams to spot and address vulnerabilities early, reducing security risks.
- Compliance: SBOMs support regulatory compliance by providing an auditable record of software components and their licenses.
- Benefits: It enables faster updates, better control over dependencies, and clearer understanding of the software’s structure.
Who Should Have A Sbom
1. Developers:
Developers need an SBOM to clearly understand every component in their software, making it easier to manage updates and troubleshoot issues. It also helps them ensure that dependencies are secure and up to date, reducing the risk of vulnerabilities.
2. Security Teams:
Security teams rely on an SBOM to identify potential vulnerabilities in software components, helping them stay ahead of threats. It gives them a clear view of what’s inside, making it easier to apply fixes and protect against risks.
3. Compliance Officers:

Compliance officers rely on an SBOM to ensure that all software components meet regulatory and legal standards, especially concerning licensing and security. It helps them verify that the software is compliant with industry regulations and reduces the risk of legal issues.
4. Organizations:
Organizations should adopt an SBOM to maintain a clear view of all software components, ensuring better control and security. It helps streamline updates, reduces risks, and supports long-term software reliability.
The Role Of Sboms In Cybersecurity And Compliance
SBOMs play a crucial role in enhancing both cybersecurity and compliance by providing a detailed map of all software components. This transparency allows organizations to quickly identify vulnerabilities and address them before they become serious threats.
In terms of compliance, SBOMs help ensure that software meets legal requirements by documenting licenses, dependencies, and other essential information. With SBOMs, companies can maintain secure, compliant software ecosystems while reducing the risk of breaches and legal issues.
1. Key Benefits of SBOMs in Cybersecurity and Compliance:
- Security Risk Management: SBOMs help identify known vulnerabilities in software components, allowing for quicker patching and mitigation.
- Regulatory Compliance: They provide an auditable trail of software components, aiding in meeting industry standards and legal requirements.
- Faster Incident Response: With a clear overview of all dependencies, cybersecurity teams can react more swiftly to threats or vulnerabilities.
- License Management: SBOMs track open-source licenses, helping companies avoid compliance issues with third-party code.
- Supply Chain Transparency: They offer insight into the software supply chain, reducing risks associated with third-party components and services.
Software Composition Analysis And Sboms
Software Composition Analysis (SCA) and SBOMs work together to enhance software security and transparency. SCA tools scan code to identify all open-source and third-party components, flagging potential vulnerabilities or outdated dependencies.
An SBOM complements this by providing a structured inventory of each component, making it easy to track and manage risks over time. Together, SCA and SBOMs offer a proactive approach to maintaining secure, compliant software.
Why Is An Sbom Important?
1. Enhances Software Security:
An SBOM strengthens software security by providing a complete list of components, making it easier to spot and address potential vulnerabilities. It allows teams to identify weak points in dependencies before they become threats. This proactive approach reduces the risk of breaches and keeps software secure.
2. Supports Compliance and Legal Requirements:
An SBOM helps organizations meet compliance by listing each software component and its licensing details. This visibility ensures that no unapproved or incompatible licenses are used, reducing legal risks. It also simplifies audits, making it easier to prove adherence to regulatory standards.
3. Improves Dependency Management:
- Tracks All Dependencies: An SBOM provides a full list of software dependencies, making it easier to monitor what’s in use and where.
- Simplifies Updates: With a clear view of all components, teams can quickly apply patches and updates, reducing downtime and security risks.
- Prevents Compatibility Issues: By understanding each dependency, teams can ensure that new updates or changes won’t break existing features.
- Enhances Maintenance: Knowing exactly what’s included in the software allows for better long-term maintenance and support.
4. Increases Transparency and Trust:
- Clear Component Tracking: An SBOM reveals each piece of software in use, building confidence in the integrity and reliability of the software.
- Enhanced Stakeholder Confidence: By openly documenting components, organizations reassure customers and partners about the quality and security of their products.
- Simplified Collaboration: Developers and security teams have a shared reference, making it easier to work together on maintenance and risk management.
- Audit-Friendly: An SBOM provides a straightforward record for audits, improving transparency and reducing compliance challenges.
SBOM Formats
- SPDX (Software Package Data Exchange): An open standard that captures detailed metadata on software licenses, helping organizations document and share component information accurately.
- CycloneDX: A lightweight SBOM format focused on security applications, providing detailed insights into components, dependencies, and potential vulnerabilities within software.
- SWID (Software Identification Tags): Standardized tags that help identify software products and versions, often used for compliance and inventory tracking.
- VEX (Vulnerability-Exploitability eXchange): A format aimed at communicating vulnerability information in SBOMs, helping teams assess and prioritize security risks effectively.
Software Bill Of Materials Best Practices

Implementing best practices for an SBOM helps maintain clarity, security, and compliance across software projects. A well-structured SBOM ensures that each component is documented and tracked, making it easier to manage dependencies and respond to risks effectively. By following these practices, organizations can enhance transparency and streamline their software management processes.
- Regular Updates: Keep the SBOM current by updating it whenever new components are added or existing ones are modified.
- Automate Creation: Use automation tools to generate SBOMs, saving time and ensuring consistency across projects.
- Include Metadata: Add relevant information like component versions, licenses, and origin to make the SBOM more informative and useful.
- Integrate with Security Scans: Link SBOMs with security scans to detect vulnerabilities in components as soon as they appear.
- Make it Accessible: Ensure the SBOM is easily accessible to all relevant team members, enhancing collaboration and quick response to any issues.
FAQ’s
1. Why is an SBOM important for security?
SBOMs let developers and security teams know exactly what’s in the software, so they can quickly identify and address any vulnerable components, reducing security risks.
2. How does an SBOM help with compliance?
An SBOM tracks each component’s license and origin, making it easier to meet regulatory requirements and avoid legal issues with third-party code.
3. Who needs an SBOM?
Developers, security teams, compliance officers, and organizations benefit from SBOMs for tracking software parts, managing risks, and ensuring compliance.
4. How often should an SBOM be updated?
An SBOM should be updated whenever new components are added or existing ones are changed, ensuring it accurately reflects the software’s current state.
5. Can an SBOM be automated?
Yes, SBOM generation can be automated using software tools, which helps maintain accuracy and consistency, especially in larger projects.
Conclusion:
A Software Bill of Materials (SBOM) serves as a vital tool for transparency, security, and control in software development. By documenting every component, it helps teams manage dependencies, spot vulnerabilities, and meet compliance with confidence.
As software grows in complexity, SBOMs become essential, providing a clear path to building resilient, trustworthy applications.