In today’s world, where cybersecurity threats are constantly evolving, organizations need advanced tools to protect their networks. One such tool is Hostscan, a feature embedded in security software like Cisco’s AnyConnect Secure Mobility Client.
Hostscan is performing a software scan to check your device for security measures like updated antivirus and active firewalls. This ensures that only secure devices can access the network. It helps keep the system safe by blocking potential threats.
This article provides a comprehensive guide on what Hostscan is, how it works, and why it’s critical for maintaining network security.
What is Hostscan?
Hostscan is a security feature designed to perform compliance checks on endpoint devices (such as laptops and mobile phones) before they connect to a corporate or secured network. It scans devices for specific security attributes, including the presence of updated antivirus software, operating system patches, and active firewalls. This ensures that only secure, compliant devices can access sensitive resources.
Why is Hostscan Important?

Hostscan plays a crucial role in maintaining the security and integrity of a network. Let’s look at why Hostscan is vital for any organization:
1. Enhanced Security
Hostscan acts as a protective layer by checking whether devices comply with security policies before granting access. This reduces the risk of malware or vulnerabilities entering the network through unsecured endpoints.
2. Compliance
Many industries, such as healthcare and finance, have strict regulations regarding data security. Hostscan helps organizations comply with these regulations by ensuring that devices meet the necessary security standards before being allowed to connect.
3. Network Integrity
By ensuring that only secure devices can access the network, Hostscan helps maintain network integrity. It prevents unauthorized devices from accessing sensitive data or compromising network security.
How Does Hostscan Work?
Hostscan operates by performing a series of checks on devices that attempt to connect to the network. Here’s a breakdown of how it works:
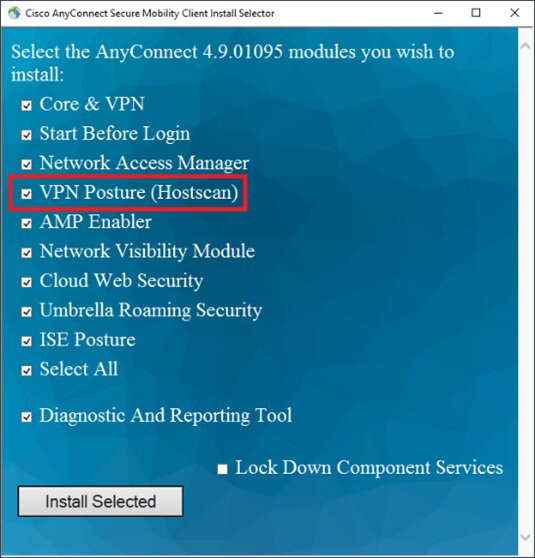
- Initiation: When a device attempts to connect to the network, Hostscan is automatically triggered. The software scan begins, ensuring that the device meets predefined security requirements.
- Assessment: Hostscan checks for several security features, such as the presence of antivirus software, active firewalls, and operating system updates. If any of these are missing or outdated, the device may be denied access or flagged for further inspection.
- Validation: Once the scan is complete, Hostscan validates whether the device is compliant with security policies. If the device passes all checks, it is granted access to the network. If not, the device may be quarantined or blocked from accessing certain resources.
Key Features of Hostscan:
Hostscan offers a variety of features that contribute to its effectiveness in securing networks:
1. Antivirus Compliance Check
Hostscan ensures that an up-to-date antivirus program is running on the device. This helps prevent malware from entering the network.
2. Firewall Status Check
A functioning firewall is essential for blocking unauthorized access and malicious traffic. Hostscan checks whether the device’s firewall is enabled and operational.
3. Operating System Updates
Hostscan verifies if the device’s operating system is up to date. Operating system updates often include security patches, which are crucial for preventing exploits.
4. Custom Checks
Administrators can configure Hostscan to perform custom checks, such as ensuring specific applications are installed or verifying encryption on the device.
Benefits of Using Hostscan:
Hostscan provides several advantages that contribute to improved network security and user experience:
1. Proactive Security
By identifying and mitigating risks before they enter the network, Hostscan allows organizations to adopt a proactive security approach, reducing the chance of breaches.
2. Improved Compliance
Hostscan ensures that devices meet security standards required by regulatory bodies, helping organizations avoid fines and reputational damage.
3. Enhanced User Experience
Hostscan operates in the background and doesn’t require manual intervention. This streamlines the security process, providing a seamless experience for users while ensuring network safety.
4. Scalability
Hostscan is scalable and can be implemented in organizations of any size, from small businesses to large enterprises, without a significant increase in administrative burden.
Common Issues and Troubleshooting:
Despite its advantages, users may encounter issues while using Hostscan. Here are some common problems and troubleshooting tips:
1. Slow Performance
If Hostscan takes longer than usual, it could be due to a large number of files being scanned or insufficient system resources. Closing unnecessary applications and performing regular system maintenance can help speed up the process.
2. Scan Failures

Scan failures may occur if Hostscan cannot access required system files or if certain permissions are missing. Ensure that the necessary permissions are granted and that no software conflicts are preventing the scan.
3. Access Denied
If Hostscan denies access to the network, it could be due to outdated antivirus software, missing firewall settings, or unpatched operating systems. Keeping your system updated can help resolve this issue.
Best Practices for Using Hostscan:
To get the most out of Hostscan, organizations should follow these best practices:
- Regular Updates: Ensure that both the Hostscan software and the security tools it checks (e.g., antivirus, firewalls) are regularly updated to maintain maximum protection.
- Policy Review: Regularly review and update the security policies enforced by Hostscan to address new threats and vulnerabilities.
- User Training: Educate users on the importance of maintaining up-to-date security software on their devices. This reduces the likelihood of non-compliance during scans.
- Testing and Validation: Regularly test and validate Hostscan’s configurations to ensure it is functioning correctly and providing accurate results.
Advanced Configuration Options:
For organizations with specific security needs, Hostscan offers several advanced configuration options:
1. Custom Endpoint Checks
Administrators can configure Hostscan to perform custom checks, such as verifying the presence of specific applications or system configurations.
2. Integration with Other Tools
Hostscan can be integrated with other security tools, such as intrusion detection systems (IDS) and endpoint protection platforms, to create a more comprehensive security solution.
3. Granular Access Controls
Hostscan allows administrators to set granular access controls based on the results of the scan. For example, devices that don’t meet certain criteria can be given limited access to the network or placed in quarantine.
Real-World Applications of Hostscan:
Hostscan is used in various sectors to ensure the security and compliance of endpoint devices:
1. Corporate Environments
Many businesses use Hostscan to protect their networks from potential threats posed by employee devices, particularly in bring-your-own-device (BYOD) setups.
2. Educational Institutions
Schools and universities rely on Hostscan to secure their networks and protect sensitive student information.
3. Healthcare

Healthcare organizations use Hostscan to ensure that devices accessing patient records and other sensitive data are secure and compliant with industry regulations like HIPAA.
4. Government Agencies
Government agencies use Hostscan to secure networks with high levels of confidentiality, ensuring only compliant devices can access classified information.
Future Trends in Endpoint Security:
As cybersecurity evolves, Hostscan and similar tools are likely to integrate more advanced technologies. Here are some trends shaping the future of endpoint security:
1. Artificial Intelligence and Machine Learning
AI and machine learning can enhance Hostscan’s ability to detect anomalies and predict potential security threats.
2. Zero Trust Security Models
Zero trust models assume that every device, regardless of its location, must be verified before gaining access to the network. Hostscan aligns well with this approach.
3. Cloud-Based Security Solutions

As more organizations migrate to the cloud, cloud-based security solutions integrated with tools like Hostscan will play a vital role in securing remote work environments.
FAQ’s
1. What is Hostscan?
Hostscan is a security tool used to check endpoint devices for compliance with security policies before they can access a network.
2. Why is Hostscan important?
Hostscan enhances network security by ensuring that only devices meeting security standards can connect, preventing potential threats.
3. What does Hostscan check for?
Hostscan checks for updated antivirus software, active firewalls, operating system patches, and custom security configurations.
4. How does Hostscan work?
Hostscan initiates a scan when a device tries to connect to the network. It checks for security compliance and validates the device before granting access.
5. What are the benefits of using Hostscan?
Hostscan provides proactive security, improved compliance, a seamless user experience, and scalability for organizations of all sizes.
6. What should I do if Hostscan denies access?
Ensure that your antivirus, firewall, and operating system are updated. Check for any custom security policies that may be causing the denial.
7. Can Hostscan slow down my system?
Hostscan may slow down your system if there are many files to scan or insufficient system resources. Closing unnecessary applications can help improve performance.
8. How can I improve the effectiveness of Hostscan?
Regularly update Hostscan and your security tools, review security policies, and train users on best security practices.
Conclusion:
Hostscan is a powerful tool for ensuring endpoint compliance and securing networks. By performing thorough scans and verifying that devices meet security standards, Hostscan helps organizations protect their data and maintain regulatory compliance. As cybersecurity threats continue to evolve, using tools like Hostscan will be essential for safeguarding corporate and institutional networks.